IMHO, a good configuration example should meet the following:
1) Minimal
No one wants to read a 300-line example. A minimal configuration is easy to understand. If needed, we may add features on top of the minimal configuration.
2) Typical
The example should represent the most popular use case.
3) No Ambiguity
Though not affecting functionality, names should be picked carefully to avoid any potential confusion for readers (especially beginners).
My goal was to set up AAA on a Cisco router with Cisco ISE for IOS CLI. Based on the username, IOS privilege level 7 or level 15 will be assigned after login.
This is a typical use case as RBAC (Role Based Access Control) is widely used. Users with privilege 7 can run most of the "show" commands but not the "conf t" command. Users with privilege 15 can run all commands.
I have ISE 1.4 and UNL 0.9.0-40 running on VMware Workstation. The topology is like below:
ISE IP = 192.168.21.131
Router IP = 192.168.21.201
Router configuration:
! -- encrypt passwords in config file
service password-encryption
!
! -- fallback user account in the event of
RADIUS failing
username admin password cisco
enable password cisco
!
! -- define RADIUS server
radius server RADIUS-ISE
address
ipv4 192.168.21.131
key secret123
!
! -- create AAA server group
aaa group server radius RADIUS-ISE-GROUP
server
name RADIUS-ISE
!
! -- creaate new AAA model
aaa new-model
!
! -- Configure the default login method to
'none' (no authentication)
! -- This method applies to the console by
default
aaa authentication login default none
aaa authorization exec default none
!
! -- Configure Authentication and Authorization methods for VTY lines
aaa authentication login VTY_authen group RADIUS-ISE-GROUP
local
aaa authorization exec VTY_author group RADIUS-ISE-GROUP
local
!
! -- Configure default Accounting method, which applies to both console and VTY lines
aaa accounting exec default start-stop group RADIUS-ISE-GROUP
!
! -- Apply Authentication and Authorization methods to VTY lines
line vty 0 4
authorization exec VTY_author
login
authentication VTY_authen
transport
input all
ISE configuration:
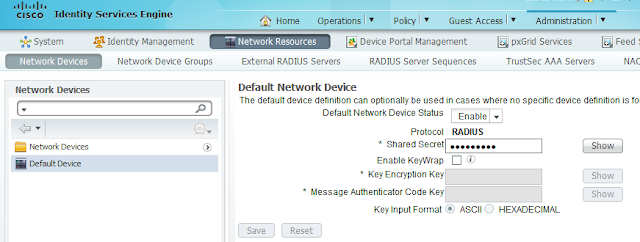
1. Administration > Network Resources > Network Devices > Default Device
For simplicity, we use “Default Device” here. You may create device group to have more
granular control.
Enable “Default Network Device Status”.
2. Policy > Policy Elements - Results > Authorization > Authorization Profiles
Create two authorization profiles:
- Shell_priv_15
- Shell_priv_7
Attribute settings for profile “Shell_priv_15”:
Cisco:cisco-av-pair
|
Shell:priv-lvl=15
|
Radius:Service-Type
|
Login
|
Attribute settings for profile “Shell_priv_7”:
Cisco:cisco-av-pair
|
Shell:priv-lvl=7
|
Radius:Service-Type
|
Login
|
3. Administration > Identity Management > Groups
Create two User Identify groups:
- CLI-users-15
- CLI-users-7
4. Administration > Identity Management - Identities > Users
Create users and put into desired group
5. Policy > Authorization
Create two authorization policies on the top:
- CLI-access-15
- CLI-access-7
Associate corresponding user group to “Conditions”
column.
Associate corresponding authorization (standard) profile
to “Permissions” column.