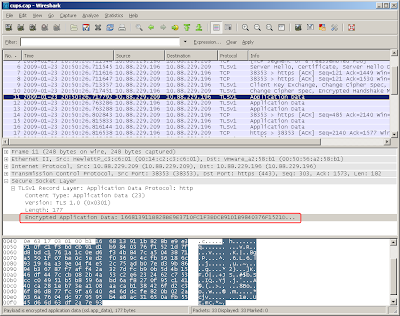
Look at packet 11 in sniffer capture above. Application data was encrypted. There's not too much useful data in it.
To decrypt this data, we need the "private key" of the server certificate. You cannot get the private key from client side (such as web browsers). To get the private key, you need access to the server.
Step 1. Export the server certificate with private key
1-1: Go to IIS Admin > Right-click "Defautl Web Site" > Properties > "Directory Security" > "View Certificate".
 1-2: Go to "Details" tab > "Copy to File" > Choose "Yes, export the private key"
1-2: Go to "Details" tab > "Copy to File" > Choose "Yes, export the private key"
1-3: You'll save the file in PKCS #12 (.PFX) with all three options UNCHECKED

1-4: You'll have to provide a password to protect the file. Because private key is a very sensitive information.

1-5: Save the file (system will add ".pfx" extension to the file name)

Now we have a PKCS #12 file (.pfx file).
Step 2: Extract the private key from .pfx file
openssl pkcs12 -in test.pfx -nocerts -out privateKey.pem -nodes
The command above take "test.pfx" as the input file, extract the private key, save it unencrypted in "privateKey.pem" file. You'll be asked for the password (where you entered on step 1-4).
Where to find openssl? Google!
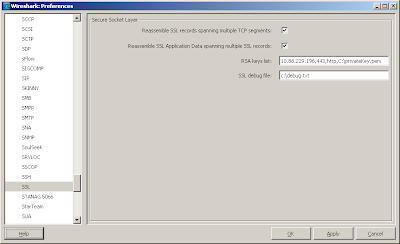
Step 3: Go to Wireshark > Edit > Preferences > Protocols > SSL. In "RSA keys list", type the following:
10.88.229.196,443,http,C:\privateKey.pem
Where "10.88.229.196" is the server IP. "443" is the port number (HTTPS). "http" is the protocol you want Wireshark decode to. "C:\privateKey.pem" is the file name of the private key. "SSL debug file" is optional.
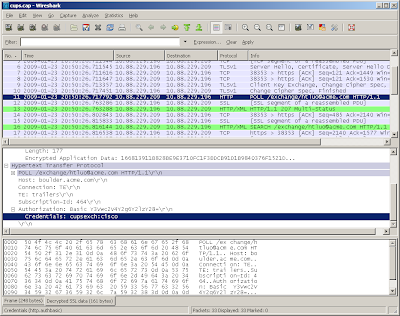
Step 4: Once you click OK, you'll notice the changes on Wireshark screen. Now the data was decrypted!


awesome information.
ReplyDeleteis there a way to get the private key from cucm so we can read the encrypted data exchanged between the cucm cluster.
-senthil
It depends on what kind of certificate you're using on CUCM. If it's a 3rd-party signed cert (such as Verisign), you (or the CUCM admin) should have the private key in that cert file.
ReplyDeleteIf you're using the self-signed cert (which is the default), you need to get, you need to get root access to the box. I can't post the details here, but you should be able to google it. :)
Once you got root access, you may use the commands below:
cd /usr/local/platform/.security/tomcat/keys
openssl pkcs8 -nocrypt -in tomcat_priv.pem -out tomcat.rsa.key
tomcat.rsa.key is the file you want
Cool. Tried it but I get an error from wireshark when trying to decode https access to ccmadmin page (ssl debug info says not enogh data to generate key)
ReplyDeleteSame thing when trying to decode CUCM -> CUPS.
Any idea ?
You have to capture the initial "handshake" of the SSL.
ReplyDeleteTry close *all* applications. Start capture. Then start application.
Did that already, closed the browser.
ReplyDeleteNow... I started an IE and it worked.
(I use Firefox by default)
Bad thing is, it does not decode CUCM -> CUPS.
Somehow the SSL decoding thing depends on the
way the client talks to the server, it seems.
-Carlos
hi! i have acces only to client side, can i got the certificate from the client?
ReplyDeletethancks
No, you cannot. This is the purpose of security.
ReplyDeletewhat if you don't have the private key? How do governments decrypt these data?
ReplyDeleteYou cannot decrypt without private key. That's the point of security.
ReplyDeletenice job~
ReplyDeleteThx a lot!